The cryptographic algorithms. Classification from the point of view number of keys

On Habrahabr already about 1000 articles or otherwise associated with the encryption, but sometimes a situation arises when you need information fast on a particular algorithm.
the
Instead of a Preface
Originally it was supposed to be a series of 3 publications, but in time the publication of the first and second in the comments I was asked to make one General article.
Unfortunately, it took more time, but now I present to You a list of about 50 algorithms, which is a reference guide with a brief description of the algorithms, and sometimes their implementation.
Of the algorithms are fairly well known, part is a Frank exotic. But it is exactly those algorithms that seemed interesting to me. Perhaps the emphasis is not on the usual things.
Special thanks to apashkova for help and editing.
Thank you in advance for feedback and suggestions.
UPD!
On the advice of Lafter post a warning.
Attention! Many of the algorithms are unsafe, outdated, etc., so their use is entirely on Your conscience. In the future when the revision of the classification will be added notes directly to each algorithm, demonstrating its safety or lack thereof.
the
Typing KA
So, I present to you an article, which contains known and not so cryptographic algorithms. I'd say this article is not meant to innovation, or uniqueness. Rather a quick reference, some even call it bedside reading. There are various classification algorithms, for example, this:
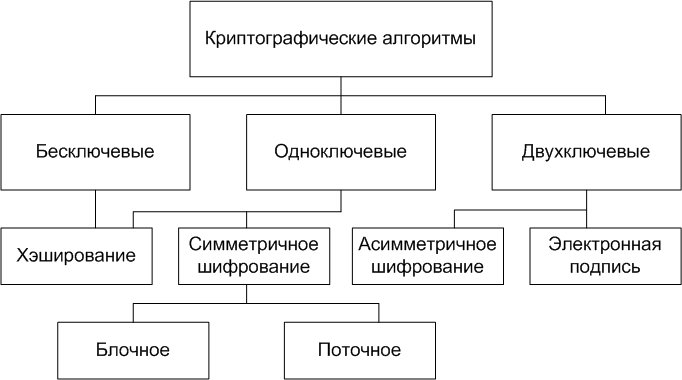
For convenience I will use the division into groups according to the number of keys:
-
the
- Keyless KA — is not used in the calculation of any keys; the
- Odnoblyudova KA — operate with one key parameter (the secret key); the
- dual-key KA — at various stages of the work are two key parameters: a secret key and the public key.
- Ciphertext, the encrypted (private) text — the data obtained after the application of a cryptosystem (usually with some specified key). the
- Key is the cipher parameter that determines the choice of specific transformations of this text. In modern cryptographic ciphers cipher strength is entirely determined by the secrecy of the key (principle Kerckhoffs).
- Encryption — the normal use of cryptographic transformation of plaintext based on the algorithm and key, which causes the encrypted text.
- Cryptanalyst is a scientist, create and use methods of cryptanalysis.
- Mitsumata protection from imposing false information. In other words, the text remains open, but it is possible to check that it has not changed neither by accident nor intentionally. Mitsumata is usually achieved by the inclusion in the package of the transmitted data kiestinki. the
- Enicostemma — a unit of information used for Kitazawa depending on key and data.
- CA — the party whose honesty is unquestionable, and the public key is widely known. The electronic signature of the certification authority authenticates the public key.
Open (source) text — data (not necessarily text) transmitted without using cryptography. the
Cipher cryptosystem is a family of invertible transformations of the plain text to encrypted. the
Decryption — the normal use of cryptographic transformation of encrypted text into the open.
Asymmetric cipher, dual-key cipher, the cipher with the public key is the cipher that uses two keys, encryption and decryption. Thus, knowing only the key to encrypt cannot decrypt the message and Vice versa.
public key — one of the two keys are asymmetric, which is freely available. Cipher for secret correspondence and decryption for an electronic signature.
Secret key, private key — one of the two keys are asymmetric, which is kept secret. the
Cryptographic attack — attempt by a cryptanalyst to cause abnormalities in the attacked secure system of information exchange. A successful cryptographic attack is called hacking or autopsy.
Decryption (decoding) is the process of retrieving the plaintext without knowledge of the cryptographic key based on the encrypted. The term decryption is usually used in relation to the process of cryptanalysis of the ciphertext (cryptanalysis itself, generally speaking, may lie in the analysis of the cryptosystem and not just encrypted it the open message).
strength is the ability of a cryptographic algorithm to resist cryptanalysis. the
digital signature, or electronic signature — the asymmetrical enicostemma (security key different from the key scan). In other words, this enicostemma that inspectors can not be faked. the
Hash function — a function that converts a message of arbitrary length and in number ("convolution") of fixed length. For cryptographic hash functions (in contrast to hash functions for General purpose) is difficult to calculate the return and find two messages with a common hash function.
the
Keyless KA
the
md2/4/5/6
MD2 is a cryptographic hash function developed by Ronald Rivest in 1989, and is described in RFC 1319. On input a message of arbitrary length. The hash size is 128 bits.
As he wrote at the time braindamagedman on MD5 and MD6:
The MD5 algorithm had once great popularity, but the first signs of cracking appeared in the late nineties, and now its popularity is rapidly declining.
The MD6 algorithm is very interesting from the structural point of view the algorithm. He was nominated for the competition for SHA-3, but, unfortunately, the authors do not have time to bring it up to standard, and in the list of candidates qualified for the second round of this algorithm, is missing.
the
Tiger
A cryptographic hash function, designed by Anderson and Roth Eli Bahama in 1995. Tiger was especially designed for fast execution on 64-bit computers. Tiger has no patent restrictions, can be used freely as reference implementation and its modifications. The size of the hash value is 192 bits (Tiger/192), although there is also a shorter version for compatibility with SHA-1 (Tiger/160) and with the MD4, MD5, RIPEMD, Snefru (Tiger/128). Speed 132 Mbps (tested with a single CPU Alpha 7000, model 660). On modern processors are much faster (even when you test on 32-bit AMD Sempron 3000+ speed of about 225 MB/s).
Also was implemented the Second version 2 —can be distinguished from the others only by adding bits algorithm similar to MD5/SHA-1. For 2 available test vectors.
the
Sha-1/2
A cryptographic hashing algorithm. Described in RFC 3174. For an input message of arbitrary length (maximum 22^64-1 bits, which is approximately equal to 2 exabytes) algorithm generates a 160-bit hash value, also called the message digest. Used in many cryptographic applications and protocols. Also recommended as the primary for public institutions in the United States. The principles underlying SHA-1, similar to those used by Ronald Rivest in the design MD4.
the
SHA-3
A hashing algorithm is a variable bit developed by a group of authors led by Yohan Dimena, co-author of Rijndael, the author of the ciphers MMB, SHARK, Noekeon, SQUARE and BaseKing. October 2, 2012, Keccak was the winner of the competition of cryptographic algorithms promoted by the National Institute of standards and technology, USA. 5 Aug 2015 algorithm was adopted and published as FIPS 202. In the software implementation, the authors claim 12.5 cycles per byte when running on a PC with an Intel Core 2. However, in hardware implementations of the Keccak was much faster than all other finalists. SHA-3 is built on the principle of cryptographic sponges.
the
Ripemd
A cryptographic hash function developed at the Catholic University of Louvain Hans Dobbertin (Hans Dobbertin), Anton Bosselaers (Antoon Bosselaers) and Bart Pranela (Bart Praneem). For an arbitrary input message function generates a 160-bit hash value called a message digest. RIPEMD-160 is an improved version of RIPEMD, which in turn used the principles of MD4 and performance comparable to the more popular SHA-1.
There are also 128-, 256 - and 320-bit versions of the algorithm with the corresponding names.
the
Haval
A cryptographic hash function designed by Yuliang Zheng, Josef Pieprzyk and Jennifer Seberry in 1992. For an arbitrary input message function generates a hash value called a message digest, which can have a length of 128, 160, 192, 224 or 256 bits. The number of iterations is variable, from 3 to 5. The number of rounds in each iteration is 32. Is a modification of MD5.
the
Now it's time odnaklacnik KA.
the
Rijndael
Also known as the Advanced Encryption standard is a symmetric block encryption algorithm. The size of one block. 128-bit, 128/192/256 keys, a standard adopted by the US government on the results of the AES competition.
Replaced the DES algorithm (described later). Specification was published on 26 November 2001. May 26, 2002 was declared the encryption standard. As of 2009, is one of the most common symmetric encryption algorithms.
Interesting fact, the key 128 provides 340 undecillion possible combinations.
the
DES
Algorithm for symmetric encryption, developed by IBM and adopted by U.S. government in 1977 as an official standard (FIPS 46-3). The block size for DES is 64 bits. The algorithm is based on a Feistel network with 16 cycles (rounds) and a key having a length of 56 bits. The algorithm uses a combination of nonlinear (S-blocks) and linear (permutations E, IP, IP-1) transformations. Recommended for DES some modes:
the
-
the
- ECB (eng. electronic code book) mode "electronic code book" (a simple replacement); the
- CBC (English. cipher-block chaining) mode block chaining; the
- CFB (eng. cipher feed back) mode feedback ciphertext; the
- OFB (eng. output feed back) mode feedback output. the
- Direct the development of the DES is currently the Triple DES algorithm (3DES). In 3DES encryption/decryption are performed by three execution of DES algorithm.
the
MMB-cipher
From eng. modular multiplication-based block cipher — modular block cipher using multiplication) block encryption algorithm based on multiplication in a finite group.
Block cipher based on multiplication in a finite group (MMB) is a block cipher developed by Yohan Dimena in 1993 as an improvement of the IDEA cipher. The main novelty of this cipher is to use the multiplication cyclic group Z2n−1. The creators of the cipher was proposed to make n=32, so the multiplication will be carried out in the group Z4294967295. It is also worth noting that the length of the words that are to be made of the operation equal to n, i.e., 32 in this case. The main goal pursued in creating this cipher to create a cipher resistant to differential cryptanalysis. Weaknesses in the key schedule was discovered by Ali Biomom that, in combination with the fact that the cipher was not protected against linear cryptanalysis have led to the use of other ciphers, for example, 3-Way cipher.
the
BaseKing
In cryptography, BaseKing is a block cipher designed in 1994 by John Demena (Joan Daemen).
It is very closely related to 3-WAY; indeed, they — variants of the same General techniques of encryption.
At BaseKing block size is 192 bits, which is two times longer than the 3-WAY. Key length is also 192 bits.
In the thesis Daemen presented a comprehensive theory of block cipher, as a fairly General algorithm cipher composed of many reversible transformations that can be chosen with considerable freedom. He discussed the security of this scheme against common known attacks, and gave two specific examples of ciphers consisting of specific choices for variables. These ciphers are 3-WAY and BaseKing. BaseKing is susceptible to the same kind of attack as a 3-WAY. Daemaen, Peeters, and van Assh also demonstrated the potential vulnerability to differential analysis, along with a small number of methods to increase the resistance of this run BaseKing such attack.
the
NOEKEON
A family of two block ciphers, developed by Yohan Dimena, Michaël Peeters, Gilles Van Assche and Vincent Ramanam and presented in a research project NESSIE. Two represent the cipher NOEKEON in direct mode (direct mode) and in indirect mode (indirect mode). The modes differ only by the extension procedure key.
The length of the key in NOEKEON is 128 bits. In each round of NOEKEON uses a sequence of transformations reverse themselves, which can easily be implemented in hardware or software, and even in this, where there is the possibility of attacks based on side channel. Cipher is a compact implementation on different programming languages, easily runs on various hardware and is very effective in a wide range of platforms. However, NOEKEON does not meet the requirements of the Wide Trail Design Strategy, which showed the cryptanalysis, carried out by Lars Knudsen and Håvard Raddum in April 2001. Knudsen and Raddum found that this cipher of a possible attack based on associated keys for which the cipher was not selected in the NESSIE project.
For consideration in the contest NESSIE was taken both modes of Noekeon algorithm. Both modes are subject to attack based on related keys, which suggested cryptology Lars Knudsen and Håvard Raddum in their work. In addition, they also proved that the criteria for the creation of substitution tables in operation Gamma does not contribute to the high cryptographic security of the algorithm: when generating a table of substitutions resulting algorithm with a probability of approximately 86% will be subject to linear and/or differential cryptanalysis. It was also shown that with high probability it is possible to find the related keys. These reasons were enough to be able to produce Noekeon algorithm to the second round of the competition.
the
DFC
Decorrelated Fast Cipher — block symmetrical cryptoalgorithm created in 1998 jointly by the cryptographers Paris Higher normal school, National center for scientific research (CNRS) and the telecommunications giant France Telecom under famous cryptologist Serge, Wadena (eng.), specifically to participate in the competition AES. It belongs to the family PEANUT (Pretty Encryption Algorithm with n-Universal Transformation) ciphers.
Block cipher with a long block of 128 bits representing the 8-round Feistel Network.
Used 64-bit encryption with eight different round keys of 128 bits obtained from a single source of key encryption. In each round, the encryption function uses the left half of the source text (block) and two 64-bit key, which is half of the corresponding round, to receive the 64-bit cipher text. Encrypt the left half of the block is added to the right. Then, according to the idea of the Feistel network, the left and right sides of the block are swapped. Decryption is the same as the encryption round distance fights keys in reverse order. The length of the original encryption key is not limited to three fixed sizes provided by the competition AES (128, 192 and 256 bits), and can be of variable size from 0 to 256 bits.
void madd(u4byte acc[4], u4byte x[1], u4byte y[1])
{ __asm {
__asm mov ecx,x
__asm mov edx,y
__asm mov eax,[ecx]
__asm mov ecx,[edx]
__asm mul ecx
__asm mov ebx,acc
__asm xor ecx,ecx
__asm add [ebx],eax
__asm adc [ebx+4],edx
__asm adc [ebx+8],ecx
__asm adc [ebx+12],ecx
}
};
#endif
the
DECIM
Decim is a stream cipher based on LFSR, developed a Lump Berbano, Oliver Billet, Ann Cantu, Nicolas Courtois, Blandina Debra, Henry Gilbert, Louis Gubina, Alin the tug, Louis Granboulan, Sederika the Lard, marine Meunier, Thomas Pornmom and Herve Seeb. Specialized for hardware implementation. Patented. Was submitted to the eSTREAM project, where it failed on the third stage.
The most important requirement to the cipher — resistance to various types of attacks. Algebraic attack is one of the most serious threats to the security of stream ciphers. If the ratio between the combination of bits from the secret key generated by her and a bit of gamma is simple or easily predictable, and finding algebraic dependencies between the combination of bits from the secret key and the bit of the key stream (gamma) is a simple task. For the complexity of the relationships between the combination of bits from the secret key (or combination of bits of the initial state of the LFSR generated by a secret key) and the key stream bits (gamma) use a nonlinear filtering function from combinations of bits of the secret key and the mechanisms of desynchronization between the combination of bits from the secret key and key stream bits (gamma). Both of these mechanisms (non-linear filter function and the mechanism of desynchronization between the combination of bits of the LFSR bits and the key stream) are the basis and the main means of preventing cryptanalytic attacks cipher Decim.
The beginning of operation of the stream cipher Decim begins with input 80-bit secret key and a 64-bit public key (Initialization Vector). Then, using certain linear combinations of bits To and bits of IV, using a nonlinear filtering function F and applying mechanism of the sample ABSG is calculated the initial state of a 192-bit LFSR. After performing all these operations, starts the generation of the key stream and filling them with a special buffer used to ensure continuous issuance of bits of to the output of the cipher where is addition modulo two binary sequence of characters of plain text.
the
MICKEY
The streaming encryption algorithm. There are two variants of this algorithm with a key length of 80 bits (MICKEY) and 128 bits (MICKEY-128). It was designed by Steve Babbage and Matthew Dodd in 2005 for use in systems with limited resources. This algorithm has a simple hardware implementation with a high degree of security. It uses irregular clocking of the shift registers, as well as new methods to ensure a sufficiently long period and pseudorandomness key sequence, and resistance to attacks. The algorithm is MICKEY participated in the bidding project eSTREAM, eCRYPT-organized community. The current version of the algorithm — 2.0. She walked in the portfolio of the eCRYPT as a stream cipher for hardware implementation.
The maximum length of a key sequence, obtained with one pair (K, IV) is 240 bits. However, it is allowed to obtain 240 such sequences when using a single K provided that IV is chosen different for each new sequence.
the
SC2000
Symmetrical block cryptoalgorithm developed by Fujitsu and University of Tokyo in 2000. The algorithm uses a 128-bit block and key length 128 to 256 bits (compatible with standard AES and supports the typical length of a key — the 128/192/256). Was recommended by the Committee CRYPTREC in 2003 for use by government agencies of Japan, but in 2013 was moved to the list of "candidates" in the recommended codes. Participated in the Nessie competition, but not in the second round, though, and showed sufficient resistance to attack — the reason was it is too complex structure and the fear of the likelihood of latent vulnerabilities.
SC2000 — cipher with a mixed structure: it uses the elements of the network Feistel and postanovachno-permutation network. The algorithm performs 6.5 (for 128-bit key), and if 7.5 (for key length 192-256-bit) rounds of encryption. Each of the rounds consists of requests to the lookup table, add the key and Keyless dvuhraundovom network Feistel.
Applied three tables the substitution: S-Box 4x4 bits used in the beginning of each round, 5x5 and 6x6 bit bit inside the Feistel network.
The extension key in the SC2000 algorithm is performed in two stages: the basis of secret symmetric key is generated the key intermediate, then the intermediate key is the right amount of fragments of the expanded key.
One round of the cipher is quite complex and consists of the following operations: Input 128-bit value is divided into 4 sub-blocks of 32 bits, each of them superimposed XOR operation of a 32-bit fragment of the extended key. The operation is performed T, which breaks the data block into 32 sub-blocks of 4 bits each.
Each 4-bit sub-block passes through the lookup table S4, which looks like this: (2,5,10,12,7,15,1,11,13,6,0,9,4,8,3,14)
The data block is divided into 32-bit sub-blocks using the transaction T’, the inverse operation T. progress overlay operation XOR of the other four fragments of the expanded key. The values of the first pair of sub-blocks are passed to the input of the function F. the result of the execution of this function results in two 32-bit values that are set by the XOR operation on the first two sub-blocks. The first pair of sub-blocks is swapped with the second pair of sub-blocks, then rerun the last step of the transformation.
the
RC4
Also known as ARC4 or ARCFOUR (the alleged RC4) — stream cipher, widely used in various systems of information protection in computer networks (e.g., SSL and TLS protocols, and algorithms security of wireless networks WEP and WPA).
A cipher developed by the company "RSA Security", and its use requires a license.
The RC4 algorithm, as with any stream cipher, built on the basis of the generator of pseudo-random bits. To the input of the generator is written in the key, and the output of pseudo-random bits are read. The key length can be from 40 to 2048 bits. The generated bits have a uniform distribution.
The main advantages of the cipher:
the
-
the
- high-speed; the
- variable key size.
RC4 quite vulnerable if:
the
-
the
- are not random or related keys; the
- single key stream is used twice.
These factors, as well as the way to use can make the cryptosystem insecure (for example, WEP).
Further, the implementation Illivion.
using System;
using System.Linq;
namespace RC4_Testing
{
public class RC4
{
byte[] S = new byte[256];
int x = 0;
int y = 0;
public RC4(byte[] key)
{
init(key);
}
// Key-Scheduling Algorithm
// Algorithm the key schedule
private void init(byte[] key)
{
int keyLength = key.Length;
for (int i = 0; i < 256; i++)
{
S[i] = (byte)i;
}
int j = 0;
for (int i = 0; i < 256; i++)
{
j = (j + S[i] + key[i % keyLength]) % 256;
S. Swap(i, j);
}
}
public byte[] Encode(byte[] dataB, int size)
{
byte[] data = dataB.Take(size).ToArray();
byte[] cipher = new byte[data.Length];
for (int m = 0; m < data.Length; m++)
{
the cipher[m] = (byte)(data[m] ^ keyItem());
}
return cipher;
}
public byte[] Decode(byte[] dataB, int size)
{
return Encode(dataB, size);
}
// Pseudo-Random Generation Algorithm
// Pseudo-random sequence generator
private byte keyItem()
{
x = (x + 1) % 256;
y = (y + S[x]) % 256;
S. Swap(x, y);
return S[(S[x] + S[y]) % 256];
}
}
static class SwapExt
{
public static void Swap<T>(this T[] array, int index1, int index2)
{
T temp = array[index1];
array[index1] = array[index2];
array[index2] = temp;
}
}
}
the
RC5
A block cipher developed by Ron Rivest of RSA Security company Inc. with a variable number of rounds, the block length and key length. It expands the sphere of use and simplifies the transition to a stronger version of the algorithm.
There are several different versions of the algorithm, in which conversion to "half-rounds" classic RC5 somewhat modified. In the classic algorithm uses three primitive operations and their inverse:
-
the
- addition modulo the
- a bitwise exclusive OR (XOR) the
- cyclic shift operations on a variable number of bits.
The main innovation is the use of a shift operation on a variable number of bits not used in earlier algorithms. These operations are equally fast on most processors, but at the same time make differential and linear cryptanalysis of the algorithm.
The encryption algorithm of RC5 consists of two stages. The procedure for the extension key and the encryption. The decryption is performed first, the procedure of the extension key, and then the inverse of the encryption procedure.
the
Rabbit
High-speed stream cipher first presented in February 2003 at the 10th FSE Symposium. In may 2005, he was sent to the eStream competition, whose goal was the establishment of European standards for in-line encryption systems.
Developers are Rabbit Martin Boesgaard, Mette Vesterager, Thomas Pedersen, Jesper Christiansen, and Ove Scavenius.
Rabbit uses a 128-bit key and 64-bit initialization vector. The cipher was designed with the purpose of use in software, as with high-speed encryption. The encryption speed can reach 3.7 cycles per byte(CPB) for CPU Pentium 3 and 10.5 cycles per byte ARM7. However, the cipher also proved to be fast and compact when implemented in hardware.
The main component of the cipher is a generator bit stream, which encrypts 128-bit messages per iteration. The advantage of the cipher thorough mixing of its inner state between two consecutive iterations. The shuffle function is completely based on the arithmetic operations available on modern processors, i.e., S-blocks lookup and search table is not needed to implement the cipher.
The authors of the cipher have provided a full set of technical descriptions on the home page of Cryptico. The cipher is also described in RFC 4503. Cryptico had a patent for a cipher, and for many years to use the code in commercial purposes required a license. However, on 6 October 2008 cipher allowed to use for any purpose free of charge.
the
NewDes
In cryptography symmetric block cryptoalgorithm, designed by Robert Cattle as a replacement of DES in 1985 with the aim of introducing a more robust cipher with secure key size of 120 bits.
NewDES, although it has a derivative name, has a completely different structure, much simpler DES, is easy to implement in software and does not include bitwise permutations, all operations are performed with bytes. The algorithm uses the replacement table of 256 elements, in the same round produced 8 operations of modulo-2 substitution using function F return using a lookup table.
The key schedule in the first edition was quite weak and was fixed in revision of NewDES-96. As it turned out, the algorithm NewDES less resistant to cryptanalysis than DES algorithm, although brute force on NewDES-96 virtually impossible and the algorithm in this edition is much more secure.
the
Salsa20
The stream encryption system designed by Daniel Bernstein (English). Russian. The algorithm was presented at the competition "eSTREAM", whose goal was the establishment of European standards to encrypt data mail systems. The algorithm became the winner of the contest in the first profile (stream ciphers for software applications with high throughput).
The Salsa20 cipher uses the following operations:
- a bitwise addition modulo 2 (xor); the
- shifts bits.
adding 32-bit numbers; the
The algorithm uses a hash function with 20 cycles. Its main transformations are reminiscent of the AES algorithm.
the
Sosemanuk
Sosemanuk is a new symmetric – oriented stream cipher, according to Profile 1 "ECRYPT call for stream cipher primitives". The key length ranges from 128 to 256 bits. The initial value is set by the capacity of 128 bits. As stated, any key length reaches 128-bit encryption. The Sosemanuk cipher uses both basic principles from the stream cipher SNOW 2.0 and some transformations derived from the block cipher SERPENT. Sosemanuk aims at improving SNOW 2.0 both in terms of security and sense of effectiveness. In particular, he uses a quick IV setup procedure. Also you need to reduce the number of static data in favor of better performance on multiple architectures(platforms).
The Sosemanuk cipher uses both basic principles of stream cipher SNOW 2.0 (the"Snow" – eng. "snow"), and some transformation(conversion), derived from the block cipher SERPENT ("SERPENT" – eng. "snake"). For this reason, its name must be associated with both a serpent and snow. However, it is well known that snow snakes do not exist since snakes either asleep, or moving to warmer climes for the winter. In addition, Sosemanuk is a popular sport common among the tribes of Eastern Canada. The idea of the game consists in throwing a wooden stick along the snow banks as possible. The name comes from the dialect of the peoples and the comparison sticks in the snow with the snake. "Kwakweco-cime win" is one of the names of these games, but it doesn't sound suitable for the name of the cipher.
the
Trivium
The algorithm is symmetric synchronous stream encryption, oriented, first and foremost, a hardware implementation with a flexible balance between speed and number of elements, having also the possibility of fairly effective software implementation.
The cipher was submitted in December 2008 as part of the portfolio of the European project eSTREAM, the profile 2 (hardware oriented ciphers). The authors of the cipher is Christophe De Cannier and Bart Preneel.
The stream cipher generates up to bits of the output stream of 80 bit key and 80 bit IV (initialization vector). This is the simplest project code eSTREAМ, which shows excellent results in cryptoleucus.
Trivium is included in the ISO/IEC 29192-3 as a lightweight stream cipher.
The initial state of Trivium is a 3 shift register the total length of 288 bits. Each step changes the bits in the shift registers by nonlinear combination of direct and feedback. To initialize the cipher key K and initializing vector IV are recorded in 2 out of 3 registers and the execution of the algorithm for 4х288 = 1152 times, which ensures the dependence of each bit of the initial state of each bit of the key and each bit of the initialization vector.
After passing the stage of initialization, each step is generated a new member of the key stream Z, which is in the process XOR with the next member of the text. The decryption procedure in the reverse order — each member of the ciphertext is the XOR procedure with each member of the key stream Z.
the
VMPC
Is a stream cipher used in some systems of information protection in computer networks. The cipher was developed by a cryptographer bartoshem Gulfcom (Pol. Bartosz Żółtak, eng. Bartosz Zoltak) as the enhanced version of the popular RC4. The VMPC algorithm is based, like any stream cipher based on a parameterized key generator of pseudo-random bits. The main advantages of the cipher as RC4 — high speed, variable size key and initialization vector (128 to 512 bits, inclusive), ease of implementation (just a few dozen lines of code).
The basis of the cipher pseudo — random number generator, the base of which is a one-way irreversible function VMPC (eng. Variably Modified Permutation Composition).
the
FROG
The algorithm is a symmetric block cipher c of an unorthodox structure, one of the participants of the American AES competition, the development of Costa Rican company TecApro Internacional.
The FROG algorithm was created in 1998 by three experts of the company Tecnologia Apropriada (Casargo) of the smaller Latin American countries, Costa Rica (previously unknown for its developments in the field of cryptography): Dianelos Georgoudis (Dianelos Georgoudis), Jlepy Damian (Damian Leroux) and Billy simón Chaves (Chaves Billy Simon).
In the contest version of the cipher meets the requirements of the AES, with a block of 128 bits and key lengths of 128, 192, or 256 bits. The algorithm theoretically allows keys with a length from 40 to 1000 bits.
The FROG cipher of put on contest international company TecApro Internacional is registered in Costa Rica. The developers of the algorithm. Georgoudis (D. Georgoudis), D. Leroux (Leroux D.) and B. Chaves (Chaves B.) — people, to put it mildly, not well known in the cryptographic world. As the authors argue, the FROG is a "new cipher with an unorthodox structure." The basis of the strength of the cipher is the secret internal key complex design, do encryption/decryption extremely easy.
In August, the TWOFISH team (Wagner, Ferguson and Schneier) have shown that the cipher key FROG can be open at work about 257.
As for the strength of the ciphers, the ratio test is much more complicated. During the preliminary assessment phase of the first round on the web site of NIST and directly at the AES2 conference was presented a considerable amount of cryptanalytic results one way or another "podmodeli" the reputation of almost all ciphers candidates. However, if you do not talk about obvious outsiders, LOKI, FROG, MAGENTA and HPC, there are no obvious weaknesses in the algorithms was not detected.
the
NUSH
Block symmetric encryption algorithm developed by Anatoly Lebedev and Alexey Volchkov for the Russian company LAN Crypto.
NUSH has several different options, with different block size (64, 128, 256 bits), variable number of rounds (depending on the size of the block is equal to 36, 128 or 132 round) and uses a key length of 128, 192, or 256 bits. The algorithm does not use S-blocks, but only such operations as AND, OR, XOR, addition modulo cyclic shifts. Before the first and after the last round is the "whitening" of the key.
This algorithm was launched in the NESSIE project, but was not selected because it has been shown that linear cryptanalysis can be more effective than the brute force attack.
On the basis of the encryption algorithm could be used to construct other algorithms. Several of them set forth in this article.
the
REDOC
Symmetrical block cryptoalgorithm developed by Michael wood in 1990 for the company Cryptech, and received the name of REDOC II. All operations, substitution, permutation, XOR are performed with bytes which allows it to effectively implement the program. The algorithm uses dependent on the key and the original plaintext sets of tables (S-boxes), using the changing table function. The algorithm is distinguished by the use of masks, i.e. numbers derived from a key table. Masks are used to select table specific functions of a particular round. When this is used as a mask value and data value.
The most effective way of opening is considered key brute force, to achieve the goal will take 2160 operations. About the only effective cryptanalysis was the autopsy of one of the rounds of the algorithm Thomas Kuzik, but to expand the opening further rounds failed. With 2300 open texts was carried out cryptanalysis of one of the rounds Shamir and Biomom, after 4 rounds was received on 3 of the mask values, but success as such it has not brought and at the moment the algorithm is considered cryptographically strong.
There is also a much simplified version of the algorithm is REDOC III, created by Michael wood. Using an 80-bit block, variable key length, can reach 20480 bits. Permutation and substitution are excluded, all operations above the block and a key based only on the use of XOR, which significantly increased the speed of encryption at the expense of resistance to differential Article based on information from habrahabr.ru
Комментарии
Отправить комментарий